Disney+, the streaming platform that puts Avengers, Jedis, and princesses all under one roof, is already a runaway success, with over 10 million subscribers. But the platform got off to a rocky start that brought to mind the famously disastrous grand opening of Disneyland in 1955: technical errors, uncompleted features, and more traffic than anticipated. Disney+ also had a distinctly 21st-century problem: thousands of its users were locked out of their accounts by hackers using stolen credentials.
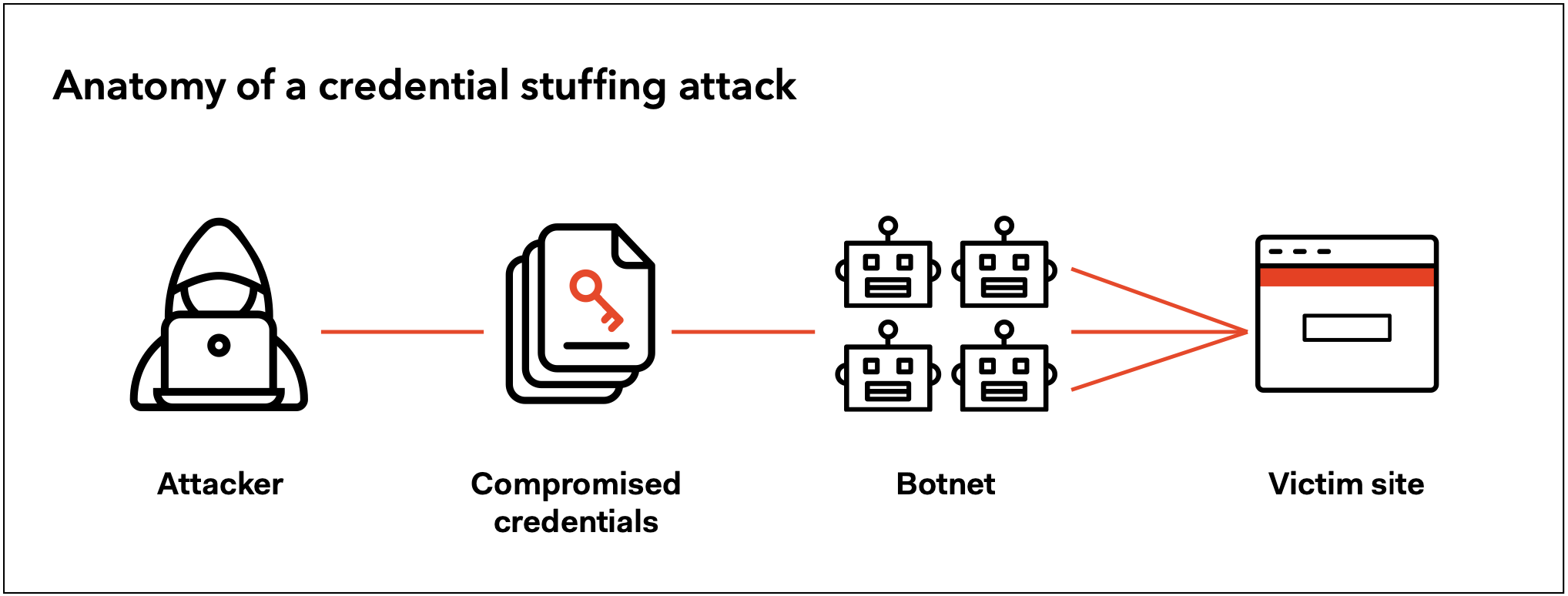
The news quickly spread that Disney+ accounts were up for sale on the dark web, where they could be purchased for less than the cost of a subscription. But Disney’s platform itself wasn’t hacked, at least not in the traditional sense. Users were the victim of a credential stuffing attack, one of the most serious and prevalent cyber threats of the moment. In credential stuffing attacks, hackers steal login credentials from one site and then use the same credentials to break into a user’s other accounts. (These attacks can also attempt to break in with overused passwords like “abc123” or the ever-popular “password.”)
Executives who want to protect their platforms from a similar attack can read on to learn what happened to Disney+ users, how credential stuffing works, and how to guard against it.
How Disney+ Accounts Were Compromised
Only hours after Disney+ went live, a small percentage of users reported that they had been locked out of their accounts, and their passwords had been changed. The legitimate subscribers whose credentials were stolen were understandably angry at losing access to the service they’d paid for, and many took to social media to vent their frustration.
DISNEY+ HAS BEEN OPEN FOR LIKE 10 HOURS AND MY ACCOUNT HAS ALREADY BEEN HACKED pic.twitter.com/YBv6CfwTlh
— brandon ʕ·ᴥ·ʔ (@brandoncult) November 12, 2019
Disney asserted that “there is no indication of a security breach,” so the cybersecurity community quickly concluded that credential stuffing was the culprit. The Disney+ victims most likely had their usernames and passwords exposed in a prior breach but were unaware that they were compromised — part of why it’s always best to use a new password for each login.
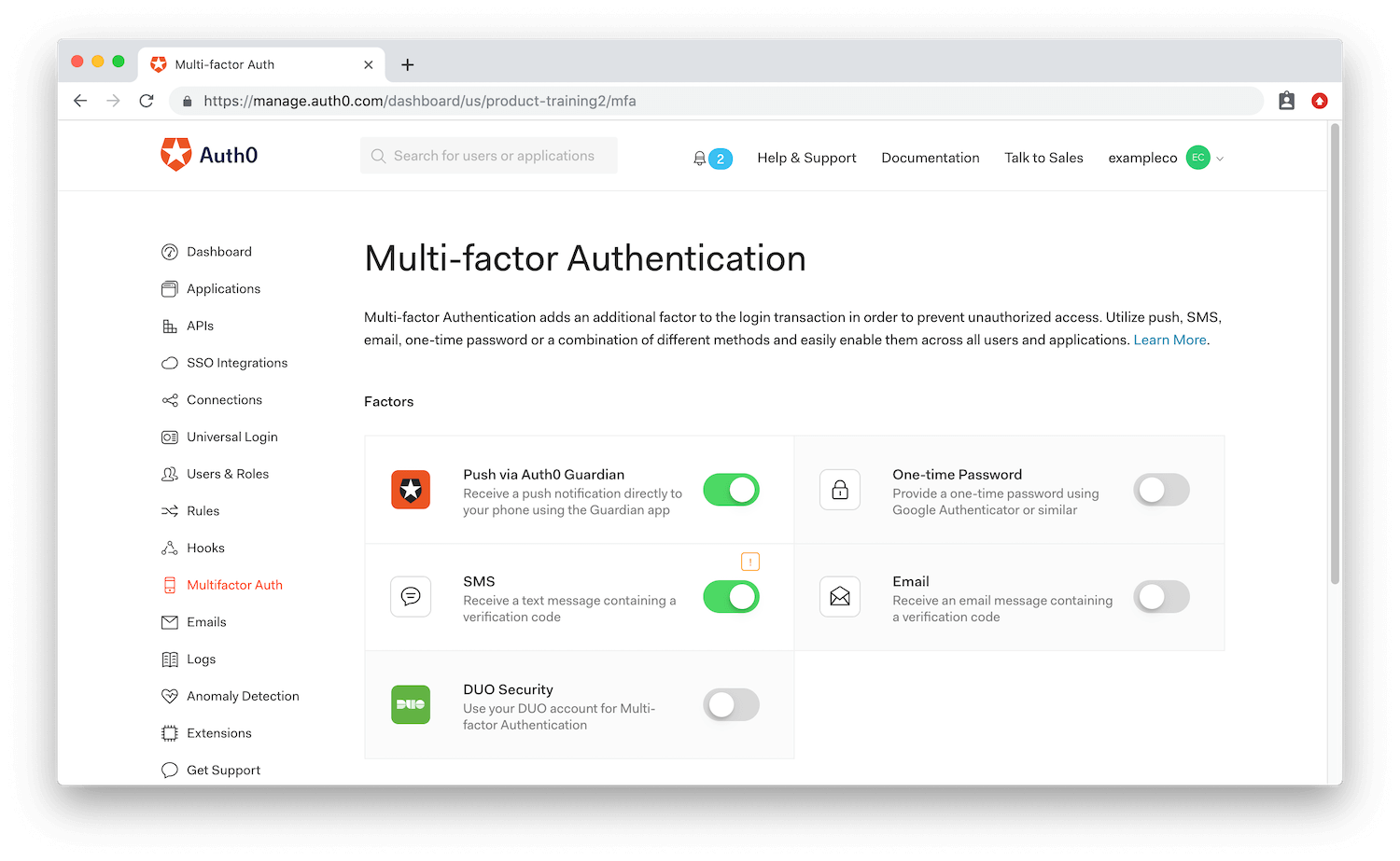
Technically, Disney+ wasn’t hacked, but they still could have done more to guard against this type of attack. Specifically, Disney didn’t have multifactor authentication (MFA) in place to act as a second line of defense. If they had, they could have requested further credentials for suspicious logins, particularly once they realized user accounts were being hacked.
"How to protect your users from a credential stuffing attack like the one that happened to @disneyplus."
Tweet This
In fairness, few streaming platforms use MFA, but the stakes were higher for Disney+ than most stand-alone platforms, given its vast web of interconnected brands. Disney allows for single sign-on across all its services, so when victims lost access to their Disney+ accounts, they also lost access to ESPN, their Disney resort accounts, etc.
What’s more, Disney+ is exactly the type of platform that hackers target in credential stuffing attacks, as we’ve seen in similar attacks at Netflix, Hulu, and Spotify.
Credential Stuffing is on the Rise
Credential stuffing is so prevalent and so successful because of the simple tendency of users to reuse passwords rather than try and remember a unique password for every service that requires a login. A McAfee survey found that the average consumer has 23 online accounts that require a password, but only use 13 unique passwords between them. According to a 2019 Google poll, 65% of Americans admit to using the same password for multiple websites, so the odds of success favor the credential stuffers.
Once a single hacker gains access to credentials, they can publish them or sell them to other criminals. The number of exposed credentials currently in circulation is staggering.
In 2018, Akamai recorded close to nacks and reported that entertainment companies were particularly vulnerable because subscriptions have market value. In January 2019, researchers discovered a trove of 2.2 billion stolen credentials being passed around the dark web, known as Collections #1-5. With this data, even unsophisticated hackers can simply test stolen passwords on different sites, hoping that a user has reused one.
"30B cred stuffing attacks in 2019 according to @akamai. Credential stuffing is increasing — what you can to protect your users."
Tweet This
Anyone with a list of stolen credentials can attempt this type of attack, but the real threat isn’t lone hackers. Large-scale credential stuffing attacks use botnets — networks of connected devices — to try thousands of possible username-password combinations.
Aside from the cost to customers, credential-stuffing attacks can cause the kind of traffic spikes that lead to website crashes. Auth0’s 2019 research found that during a credential stuffing attack, website traffic can increase by 180 times its normal volume. And these attacks are constant and unrelenting; on a typical day, credential-stuffing attempts comprise nearly half of all login requests made on Auth0. Tracking and thwarting these attempts is a critical function of any worthwhile identity and authentication management (IAM) solution.
How Businesses Can Guard Against Credential Stuffing
For the foreseeable future, it’s safe to assume that users will continue to recycle passwords, no matter how much websites try and discourage the behavior. But that doesn’t mean that businesses are powerless against credential stuffing. There are some straightforward ways to protect accounts without abandoning the username-password login model altogether.
As we mentioned above, MFA is effective at stopping credential-stuffing attempts. With MFA, businesses can set the parameters that will trigger a request for further identification (such as a one-time code). If a user logs in from a new device, for example, or performs a sensitive task, such as changing payment information, they’ll have to prove they are who they claim to be.
Streaming and media apps aren’t the only businesses who can benefit from an MFA solution; The National Institute of Standards and Technology (NIST) recommends that e-commerce businesses implement MFA to protect against credential stuffing.
Auth0 offers highly customizable MFA solutions, so businesses can choose both the method of authentication and the behaviors that will require additional credentials to balance security with frictionless customer experience.
In addition to MFA, Auth0 offers breached password detection. This feature works by keeping a constantly updated database of breached credentials and proactively notifying users when their information has been compromised. If they choose, businesses can mandate that users can’t log in again until they reset their password.
Protect your Customers and your Reputation from Hacks
Disney+ was not directly to blame for its customers losing access to their accounts, but the attack nevertheless tarnished the debut of their hotly anticipated platform. Executives who want to avoid seeing their company in the headlines for a similar attack must be proactive in placing appropriate safeguards. A qualified IAM partner like Auth0 can help in determining the right safeguards for your company, so you’ll have more standing between hackers and users than “password123.”
To learn more about credential stuffing attacks and how to defend against them, download our whitepaper.