Inbound SCIM for Okta Workforce SAML Connections
Before you start
Create a SAML Connection in your Auth0 tenant and connect it to a corresponding custom SAML application in your Okta Workforce Identity Dashboard.
This section describes how to configure a custom SAML and SCIM app integration in an Okta Workforce Identity tenant, which can be used to provision users to your Auth0 SCIM endpoint.
Configure SCIM settings in Auth0
Launch the Auth0 Dashboard and go to Authentication > Enterprise > SAML > [Connection] > Provisioning.
Disable Sync user profile attributes at each login unless you want to sync additional attributes at login.
In the same section, enable Sync user profiles using SCIM.
Under the Mapping tab, ensure the SCIM attribute containing the User ID setting is set to userName.
Review the Additional Mappings to ensure the extended SCIM attributes are mapped to your preferred Auth0 attributes, reviewing attribute mapping for details. If you receive phone numbers and physical addresses, note that Okta Workforce sends these as
phoneNumbers[primary eq true].valueandaddresses[primary eq true].*by default.Map the SCIM
userNameattribute to the Auth0emailattribute so Okta can find and match existing users if this connection has already been deployed to production using the email address as the login ID and no Auth0usernameattribute is set on the existing user profiles. In Additional Mappings find the following attribute pair:Replace it with the one below, then remove the mapping to{ "scim": "userName", "auth0": "username" }Was this helpful?
/emails[primary eq true].value.{ "scim": "userName", "auth0": "email" }Was this helpful?
/Choose Save Changes.
Retrieve SCIM endpoint URL and token
In the Auth0 dashboard, browse to the SCIM Setup tab and copy the SCIM Endpoint URL, then paste it somewhere safe.
Select Generate New Token and set an optional expiration date for the token. You can optionally select the scopes you want to grant to Okta Workforce; the default scopes used by Okta Workforce are
get:users,post:users, andput:users.
Configure SCIM in Okta Workforce for SAML Apps
Go to your Okta Workforce Identity SAML application, select the General tab, then choose Edit for App Settings.
In the Provisioning section, select SCIM and then Save.
Under the General tab, also confirm that Federation Broker Mode is disabled.
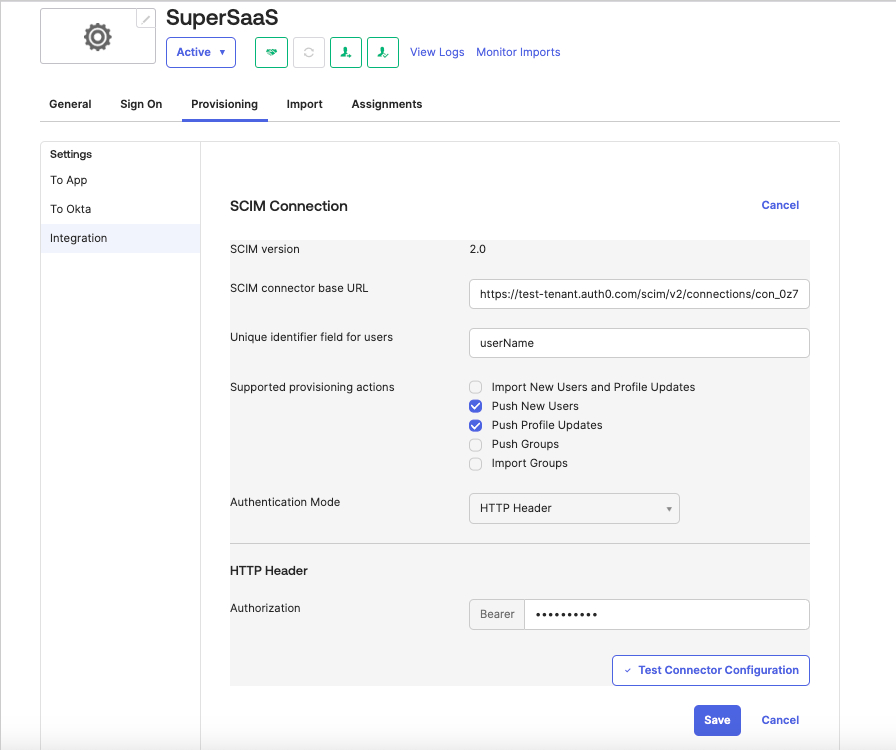
Select the Provisioning tab, then go to Integration tab and select Edit.
Enter the SCIM Endpoint URL value you copied earlier into the SCIM connector base URL section.
For Unique identifier field for users, enter userName.
Under Supported provisioning actions, select
Push New UsersandPush Profile Updates, then choose HTTP Header as the Authentication Mode.Paste the SCIM token into the Authorization field, then choose Test Connection Configuration if you want to test the new connection. Select Save.
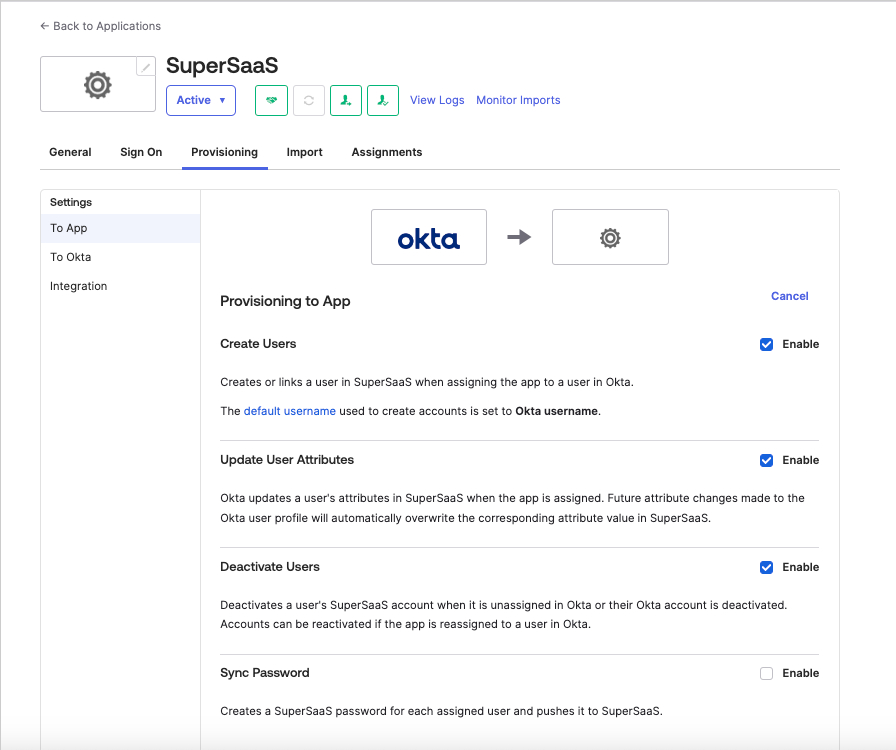
Browse to Provisioning > Settings > To App and choose Edit, then enable the Create Users, Update User Attributes, and Deactivate users operations. Select Save.
8. Under the Attribute Mappings section, use the X button to delete the following lines:
| Attribute | Value |
|---|---|
| Primary email type | (user.email != null && user.email != '') ? 'work' : ‘' |
| Primary phone type | (user.primaryPhone != null && user.primaryPhone != '') ? 'work' : ‘' |
| Address type | (user.streetAddress != null && user.streetAddress != '') ? 'work' : ‘' |
Use the Attribute Mappings section to configure any additional SCIM attributes you want Okta WIC to send to your SCIM endpoint. If you add custom attributes, they must include a valid SCIM 2.0 external namespace property. For more information on external namespaces, read Okta's help section.
You can now test user provisioning in the Assignments tab and test update operations by editing the user attributes in the Directory > People section of your Okta admin portal.

