Configure Heroku as SAML Service Provider
Use the following SAML configuration for Heroku.
Configure SAML SSO in Auth0
Go to Dashboard > Applications > Applications and either create a new application or click the name of an application to update.
Go to the Addons tab and enable the SAML2 Web App toggle.
On the Settings tab, set the Application Callback URL to the ACS URL for your organization from the Settings page in the Single Sign-On section in Heroku.
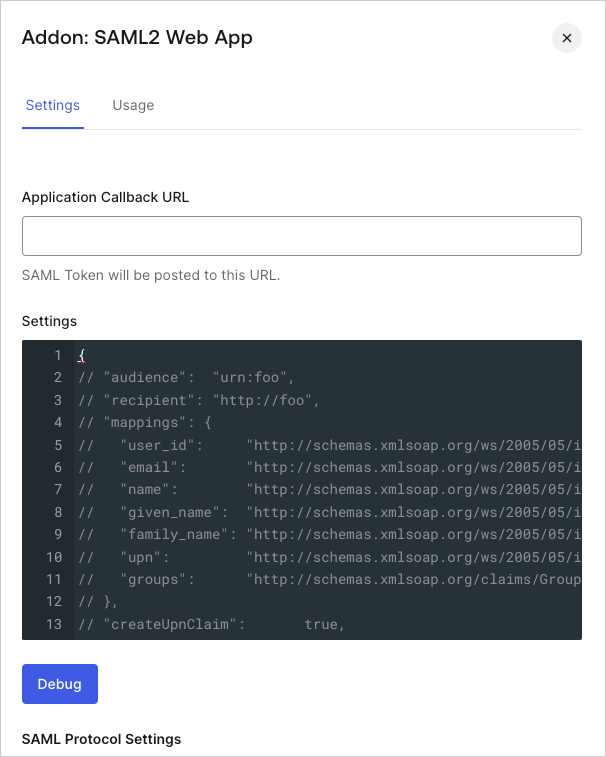
Paste the following code into the Settings text box and click Debug.
The{ "audience":"THE-HEROKU-ENTITY-ID", "mappings": { "email": "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress" }, "createUpnClaim": false, "passthroughClaimsWithNoMapping": false, "mapUnknownClaimsAsIs": false, "mapIdentities": false, "nameIdentifierFormat": "urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress", "nameIdentifierProbes": [ "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress" ] }Was this helpful?
/audienceparameter is the Heroku Entity ID from the Settings page in Heroku. It will be formatted like this:https://sso.heroku.com/saml/{yourHerokuOrg}.Scroll to the bottom of the page and click Enable.
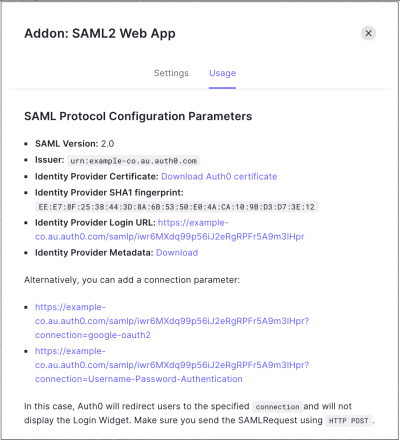
On the Usage tab, locate Identity Provider Metadata, and click Download to download the metadata file. You'll need this when you configure Auth0 as the identity provider in Heroku.
Configure SAML SSO in Heroku
In Heroku, on the Settings page in the Single Sign-On section, click Upload Metadata and select the file containing the Identity Provider Metadata you downloaded in the previous step.

