Auth0 supports authentication through a ton of different providers. Through social login, our user's users can connect via Google, Twitter, Facebook and a host of others. Auth0 also provides authentication for Enterprise clients through LDAP, Microsoft, and Google among others.
Throughout 2015 we collected data on how companies and individuals were using these providers with Auth0. We wanted to know how our users were using Auth0 and how their users were using Auth0. Which providers were the most used and how was their share changing over time.
In this second article we are looking at which Enterprise providers are most used via Auth0, how often Enterprise connections are used, and how developers can use better connections to boost security, usability and value for users.
Here’s what we found.
What Connections Are Enterprise Using?
Auth0 has a number of Enterprise connections available to users easily from the Dashboard:
Using these allows companies to let their users connect via enterprise credentials, access internal identity providers to validate these credentials, and implement single sign on (SSO) easily for their users.
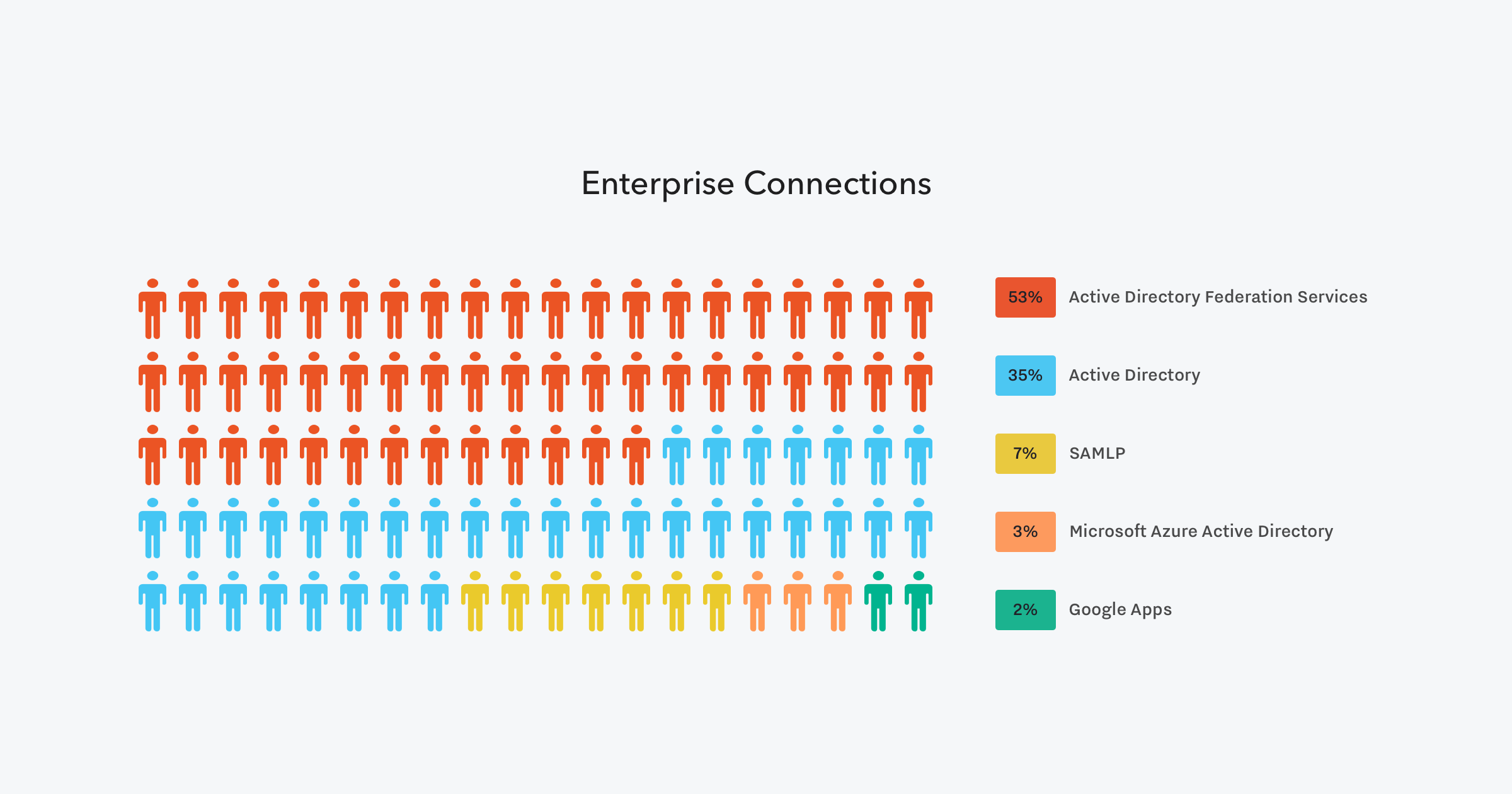
We wanted to see which of these possible connections was most common among Enterprise users:
Findings:
- Most (53%) Enterprise connections are through Active Directory Federation Services (ADFS).
- Another 35% are using Active Directory connections.
- SAMLP (7%), Microsoft Azure Active Directory (3%), and Google Apps (2%) round out the top 5.
These results show that logins via Windows Server architecture are still by far the most common connections made by Enterprise. These results tally with what we have said before—hundreds of thousands of companies rely on Active Directory. In fact, over 90% of all Enterprise connections through Auth0 are built on Windows architecture, either through AD directly, Microsoft Azure, or via Office 365 or Sharepoint.
“Over 90 percent of all Enterprise connections through Auth0 are built on Windows architecture.”
Tweet This
ADFS is the part of Active Directory Services that allows for resource access across traditional boundaries:
- It provides simplified and secure identity federation.
- It enables the creation of trust relationships between two organizations.
- Provides access to applications between organizations.
- Provides single sign on between two different directories for web-based applications.
In this way, it acts as an easy and transparent way for a user in one organization to connect and access applications from another organization.
However, because Active Directory was designed to work on the internal corporate network, it isn’t best-suited for web-based services.
Why People Use Microsoft Azure Active Directory through Auth0?
One of the perks of using Auth0 with Microsoft Azure Active Directory is that you gain access to more features not available in AAD standalone. By combining AAD with Auth0 you can take advantage of all our available SDKs and a better development experience.
Whether you are just getting started or already deep into a project - our SDKs will help you quickly integrate a solid authentication framework into your application. We provide SDKs for most major languages and frameworks including Angular, Node.js, ASP.NET, Java, and more. Our selection of quickstarts, seed projects, and tutorials showcase best practices and how-to’s to ensure you are up and running as quickly as possible.
You also get access to rules, which are JavaScript code snippets that allow easy control and customization of the login process. Rules are an easy way to address that inevitable exception in an identity environment – integration with marketing or analytics tools, whitelisting and other forms of access control, triggering a webhook, and so on. You can check the Rules documentation for more information.
How Much Are Enterprise Connections Used?
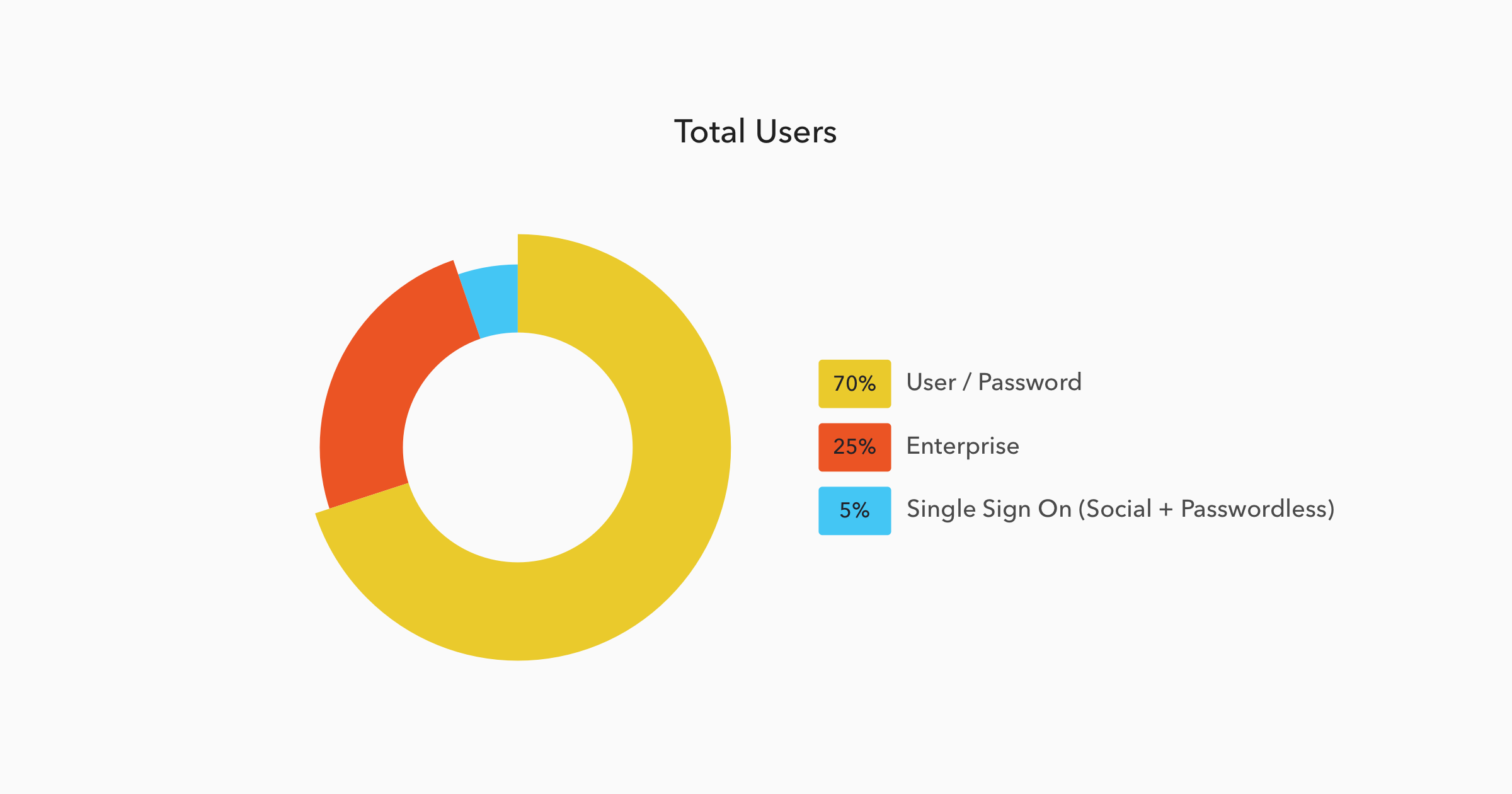
Enterprise connections are only a small part of the possible login options available through Auth0. We wanted to see what proportion of the total logins were Enterprise compared to these other options:
Findings:
- An astonishing 70% of all logins still use username and password combinations.
- Enterprise connections account for almost a quarter (24.7%) of all logins.
- Passwordless logins currently account for less than 1% of all logins.
So 1 in 4 connections made through Auth0 are using an Enterprise connection. From this we can surmise that a significant number of Auth0 users are B2B companies, looking to make it easier for the employees of other companies to use their apps.
This is excellent news. One of the best ways for developers to grow their revenue is to add Enterprise options to their existing app, such as the ability for companies to login with their current Enterprise connections.
What is less excellent news is that Enterprise connections, as well as social and passwordless, are still dwarfed by the traditional username and password combination. This means lower security, reduced compliance, and reduced B2B collaboration for those companies and users.
Conclusion
There are two major findings from our study so far:
- The vast majority of Enterprise connections are using Windows Active Directory in some capacity.
- The vast majority of users are still using an individual username and password combination.
Both of these are areas of improvement. Auth0 users currently connecting through AD or ADFS could start to look seriously at using Azure for their connections instead. And Auth0 users not pushing their own users away from unique usernames and passwords should definitely consider allowing SSO, either through Enterprise or Social.
About the author

Diego Poza
Sr Manager, Developer Advocacy (Auth0 Alumni)