Companies of all sizes are under attack, targeted by numerous phishing attacks that are coming at an ever-increasing rate. Even if the tech industry continues to improve how organizations identify and defend against those attacks, the problem is bigger than ever. According to ProofPoint's 2020 State of The Phish Annual Report, 88% of organizations faced a targeted phishing attack in 2019, and 65% of US organizations experienced a successful phishing attack.
There are options for decreasing the chances of successful phishing attacks targeting your company. Things like employee training and security policies, such as using password managers and enforcing multi-factor authentication (MFA), are all steps in the right direction.
However, if you want to neutralize the threat completely, you need to enable authentication methods that cannot be phished. That's what Google did in 2017 to neutralize phishing of its employees. Google now requires all employees to use U2F Security Keys to authenticate to corporate websites.
U2F evolved into the WebAuthn specification, which is now supported by the latest versions of browsers and operating systems. Auth0 is now supporting WebAuthn with FIDO security keys for multi-factor authentication. You can start protecting your users with Auth0 today, using the same technology as Google.
About WebAuthn
The Web Authentication API (also known as WebAuthn) is a specification written by the World Wide Web Consortium (W3C) and The Fast IDentity Online Alliance, known as FIDO, with the participation of Google, Mozilla, Microsoft, Yubico, and others. The API allows servers to register and authenticate users with public-key cryptography instead of a password.
When it comes to security, many people think you have to sacrifice security in the name of user experience, and vice versa. However, the key to maximizing both variables is to reduce the number of times we prompt the user for authentication and to allow the user to authenticate with secure factors that provide low friction. WebAuthn promises to be the holy-grail of authentication factors, as it accomplishes exactly that by combining maximum security with a low-friction user experience.
WebAuthn allows users to authenticate using one of two options:
Roaming authenticators — These are removable and cross-platform devices, like a Yubikey that can be used on multiple devices. To authenticate with a roaming authenticator, you simply connect it to the device (through USB, NFC, or Bluetooth), provide proof of presence (e.g., touching it), and optionally an additional authentication factor like a PIN or fingerprint recognition.
Platform authenticators — This option includes the MacBook's TouchBar, Windows Hello, iOS Touch/FaceId, and Android's fingerprint/face recognition. Integrated into the device being used, these only work on that device.
When doing multi-factor authentication, we want to challenge the user with something they know (like a password), something they have (like a security key), and something they are (e.g., their fingerprint).
Note that a Roaming Authenticator + PIN combines two factors in one (you have the key, and you know the pin), and a Platform Authenticator also does (you have the device, you are the person with that fingerprint/face, or you know the passcode).
In recent months the WebAuthn API has been implemented in major browsers and operating systems, enabling support for both options.
Want to learn more about WebAuthn?
Visit → webauthn.me
The Case for Security Keys
Using a Security Key allows you to authenticate users with the strongest possible authentication factor. This helps you to solve several problems at once by:
- Protecting sensitive data and employee accounts
- Providing secure access from outside the corporate network
- Allowing your employees to authenticate to shared computers
- Enabling MFA in scenarios where users cannot carry their mobile phone
It also offers several advantages when compared with using a smartphone only authenticator for MFA:
- Protects against phishing and man-in-the-middle attacks
- Strengthens user privacy as it doesn't require a personal device
- Provides one-touch login without having to take your mobile phone to complete an authentication challenge
- Has no battery or signal dependency
- Has no moving parts, so it's practically indestructible
- Allows users to register multiple keys, minimizing business disruption and the chances of account lockout
WebAuthn With Security Keys for Multi-Factor Authentication
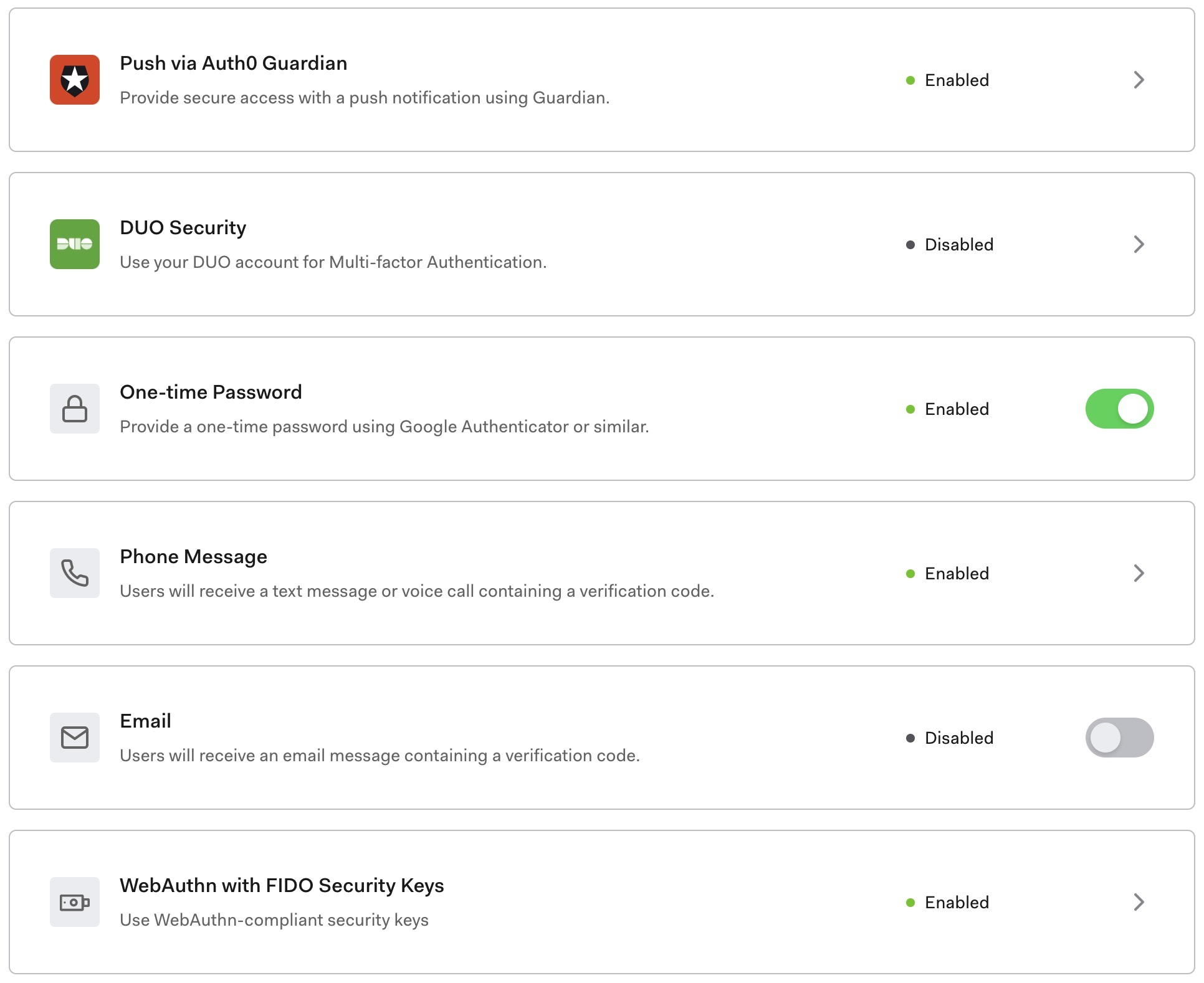
Auth0 with WebAuthn support for Security Keys is available starting today. You can enable the factor in the WebAuthn with Security Keys MFA configuration section of the admin dashboard:
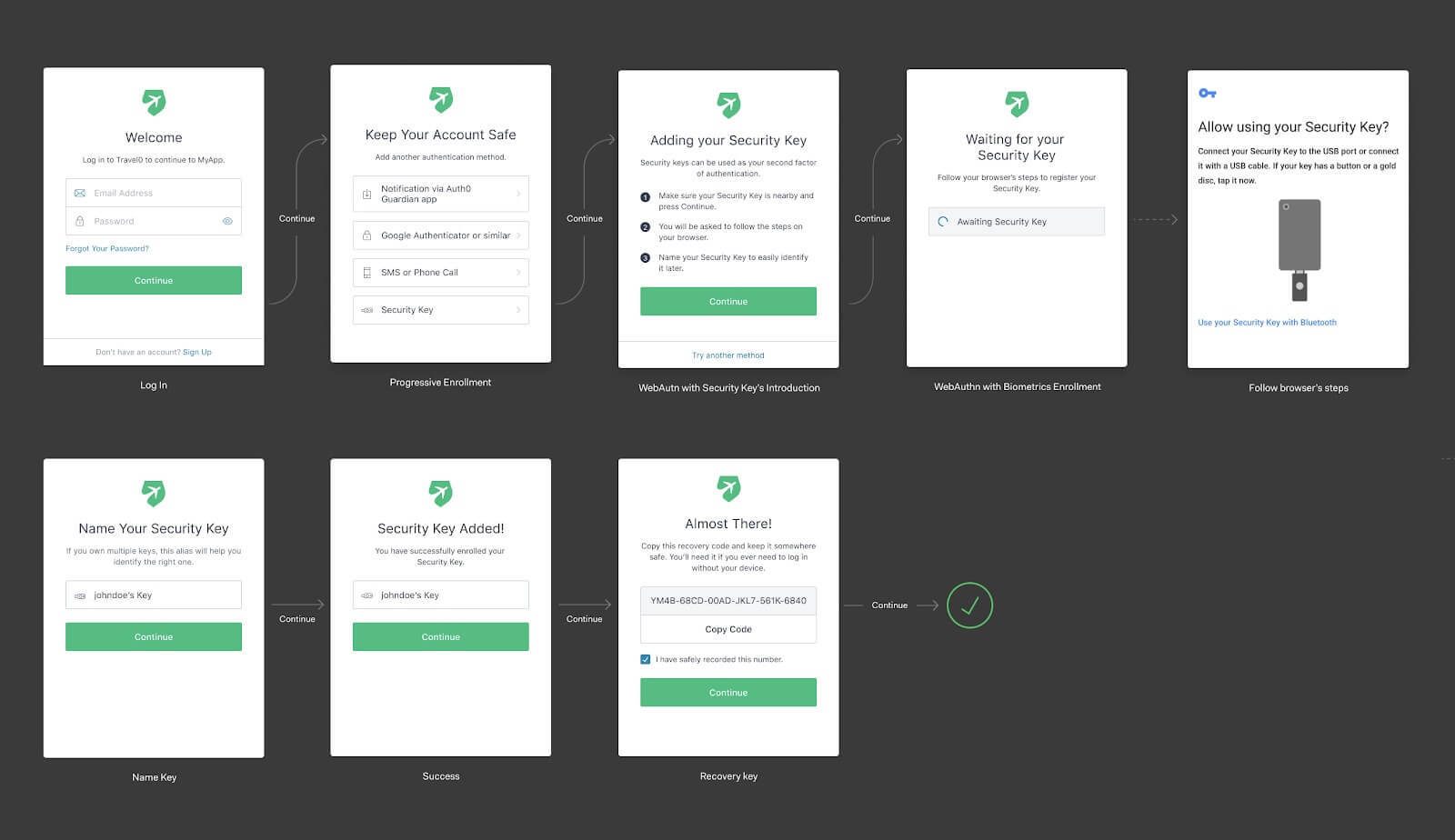
After it is enabled, users will go through the enrollment flow below. At some point, their browser will show a native dialog to ask users to engage the security key. In the example below, we show the Android dialog:
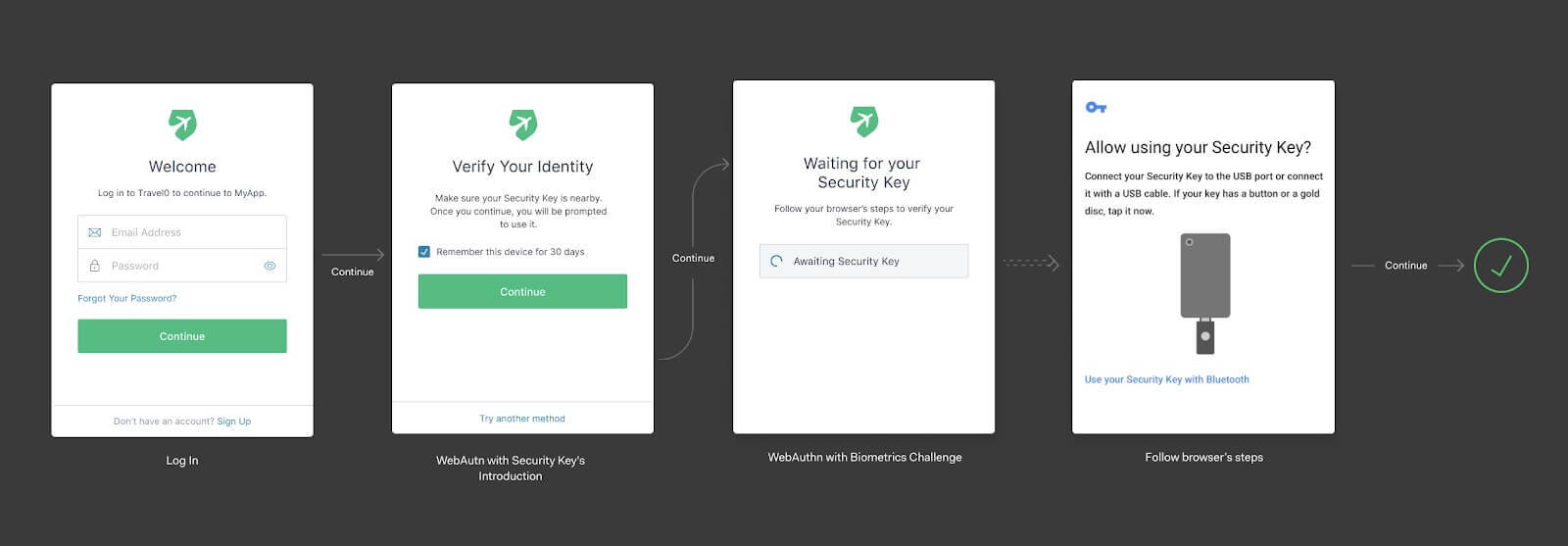
The next time they login, the flow will look like this:
Stay Tuned!
In addition to supporting WebAuthn with roaming authenticators, we are currently working on a unique approach that will greatly improve the usability and adoption of WebAuthn platform authenticators. Check out Vittorio Bertocci's session "Democratizing WebAuthn for Developers and End Users" from FIDO's Authenticate conference for the scoop!
WebAuthn is an exciting technology, and Auth0 is committed to providing the best possible implementation, maximizing security without sacrificing user experience. Check out our new WebAuthn offering and let us know what you think on our Feedback page or in the Auth0 Community.
About Auth0
Auth0 by Okta takes a modern approach to customer identity and enables organizations to provide secure access to any application, for any user. Auth0 is a highly customizable platform that is as simple as development teams want, and as flexible as they need. Safeguarding billions of login transactions each month, Auth0 delivers convenience, privacy, and security so customers can focus on innovation. For more information, visit https://auth0.com.
About the author

Andrés Aguiar
Product Manager
I’ve been at Auth0 since 2017. I’m currently working as a Product Manager for the Auth0 FGA and OpenFGA products. Previously, I worked in the teams that owned the Login and MFA flows.
I spent my entire 20+ year career building tools for developers, wearing different hats. When I'm not doing that, I enjoy spending time with my family, singing in a choir, cooking, or trying new kinds of local cheese.