As developers, we're building the next generation of applications on a foundation of interconnected services. The Model Context Protocol (MCP) is rapidly becoming a key part of that foundation, enabling seamless context sharing between AI models and applications. But as adoption grows, how do we ensure the connections we build are secure?
The latest changelog, released on June 18, 2025, introduces updates that clarify how authorization should be handled for MCP Servers and how MCP Clients should implement Resource Indicators to prevent malicious servers from obtaining access tokens.
Let's break down what’s new for auth and what it means for you as you build with MCP.
MCP Servers Now Classified as OAuth Resource Servers
MCP servers are now officially classified as OAuth Resource Servers. This might seem like a small semantic change, but it has significant implications for security and discovery.
By defining MCP servers this way, the protocol now includes a mechanism to add protected resource metadata. What does this mean in practice? It allows an MCP server to advertise where its corresponding Authorization Server is located. This discovery mechanism is vital for clients, as it removes ambiguity and ensures they request tokens from the legitimate, intended authority, streamlining the authorization process securely.
Preventing Token Misuse by Implementing Resource Indicators (RFC 8707)
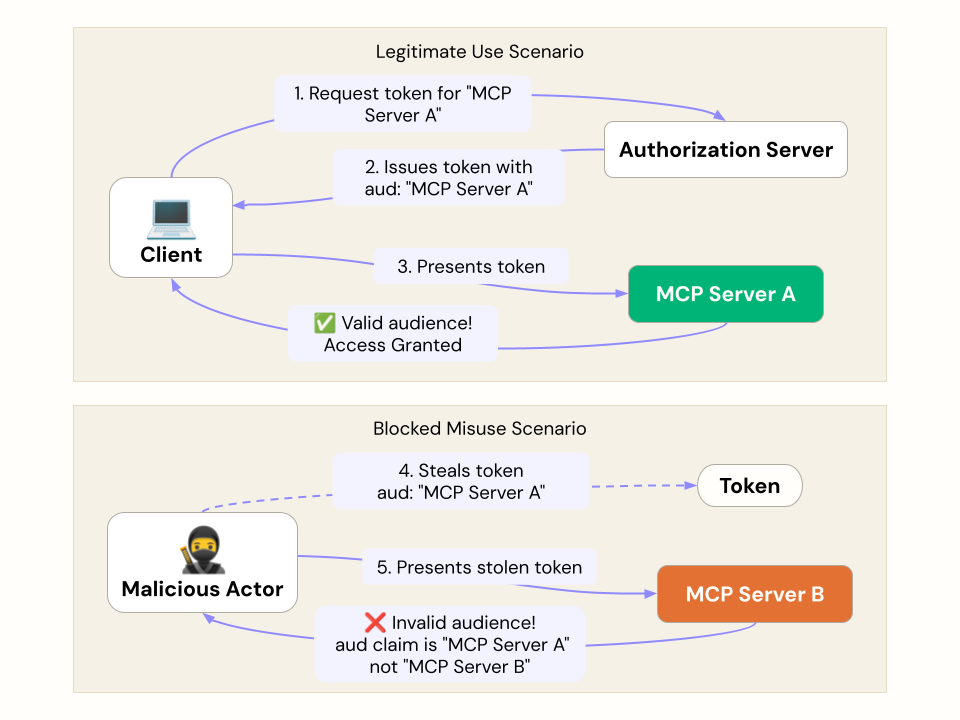
Have you ever worried about a token intended for one service being misused at another? This is a legitimate threat known as "token mis-redemption." To combat this, MCP clients are now required to implement Resource Indicators, as specified in RFC 8707.
By using a resource indicator in the token request, a client explicitly states the intended recipient (the "audience") of the access token. The Authorization Server can then issue a token that is tightly scoped and only valid for that specific MCP server. This prevents a malicious or compromised server from taking a token it received and using it to access a different protected resource on the user's behalf. Put plainly, this practice ensures your tokens can't be used where they don't belong.
Clearer MCP Security Guidance and Best Practices
Building secure systems is easier when the rules of the road are crystal clear. This update brings significant clarifications to the core authorization spec's security considerations and introduces a brand new, dedicated page for security best practices.
This new guidance provides actionable advice for developers like you and me so we can implement both clients and servers more securely. It centralizes security guidance, making it easier to build robust and secure MCP integrations from the ground up. We strongly recommend all developers working with MCP review these pages.
Building a More Secure Future
These updates represent a significant step forward in hardening the Model Context Protocol. By formalizing the roles of servers, mandating token protection with resource indicators, and providing clearer documentation, the MCP is becoming an even more robust and trustworthy standard for the AI application ecosystem.
While these aren’t the only changes in the June 18th MCP specification changelog, they are the most impactful ones concerning authentication and authorization. If you are building and securing MCPs you should check out our documentation on Auth for MCP and the Getting Started with Auth0 Model Context Protocol (MCP) Server.
Now you’re ready to go forth and enhance the security of your MCP servers and clients.
About the author

Jessica Temporal
Sr. Developer Advocate