AI agents are no longer just chatbots answering trivia questions. They’re writing code, querying APIs, scheduling meetings, and even collaborating with other agents to accomplish tasks. As this evolves, developers are starting to ask: how do these agents actually work together? Two concepts come up a lot: Model Context Protocol (MCP) and Agent-to-Agent (A2A) communication. Both terms show up often in AI architecture conversations, but they’re often discussed in different contexts or with varying levels of technical depth. In this post, we’ll unpack both concepts side by side in plain language, with practical context for developers.
What Is Model Context Protocol (MCP)?
MCP (Model Context Protocol), developed by Anthropic, is a structured way to let AI agents access tools, APIs, or external resources. It acts like a universal toolbelt, giving agents a predictable way to understand what tools are available, how to use them, and what to do with the responses. This makes tools safe, structured, and reusable across different models or vendors.
It works by connecting an MCP client (typically the LLM-powered agent) to local data sources and/or remote resource servers, which manage access to external tools or datasets.
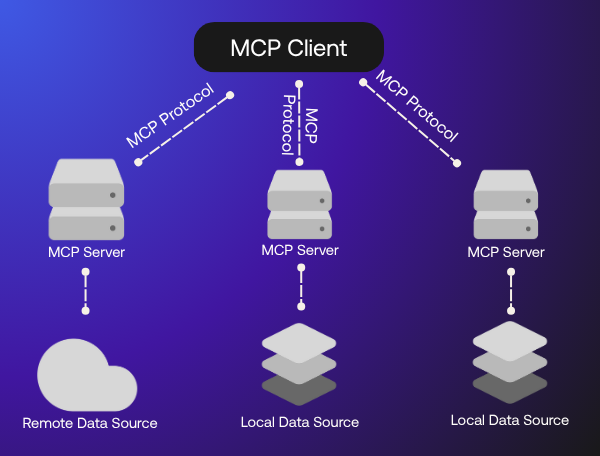
How MCP works
At a high level, MCP is about helping an AI agent figure out what tools it can use, what they do, and how to call them safely. It’s like setting up a toolbox and giving the agent an instruction manual, instead of poking random APIs.
Here’s how a typical flow might go:
- The user asks something the agent can’t answer with its current knowledge.
- It realizes it needs outside info, like data from an API or a tool to crunch numbers.
- If required, the user gets prompted to approve access.
- The agent sends a structured request to the MCP server asking for what it needs.
- The MCP server checks if the agent has permission and returns the result.
- That fresh data or tool output gets added into its working memory.
- Now the agent can respond with more accuracy and context.
MCP simplifies tool access and enforces safe, structured use of external resources without requiring the agent to understand the internal workings of those tools.
Learn more about MCP by reading this introduction blog post.
Discover the Model Context Protocol (MCP) and its authorization mechanisms. Learn how to use API keys, OAuth 2.1 implementation, and best practices for secure LLM API connections.
What Is Agent-to-Agent (A2A) Communication?
Agent-to-Agent (A2A) communication, a concept being defined by Google Cloud, is like agents chatting with each other to figure things out together sharing goals, dividing up work, and sometimes even debating the best way forward. It's more like teamwork than just calling tools, and it opens the door to more dynamic, flexible problem-solving.
In A2A, agents typically fall into one of two categories:
- Client agents initiate requests and coordinate tasks on behalf of the user.
- Remote or Service agents advertise specific capabilities and handle incoming requests.
This simple distinction helps keep communication clear and makes it easier for agents to find the right collaborators.
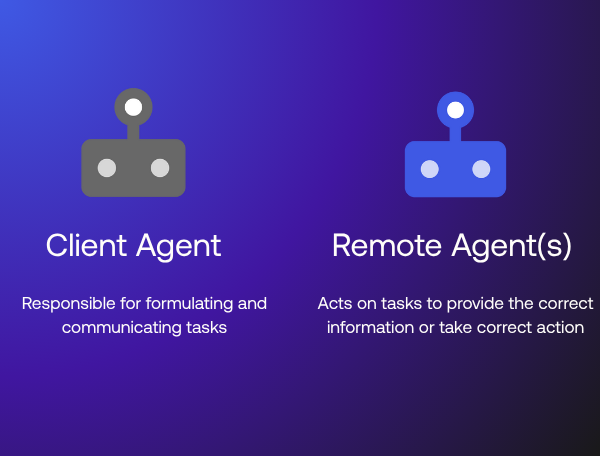
How A2A works
A2A is all about letting agents talk to each other using standardized protocols. These agents send and receive JSON messages over HTTP, often mediated by an A2A server. But before that can happen, there needs to be a layer of trust.
That’s where Agent Cards come in, self-descriptions that each agent publishes outlining what they can do, what protocols they speak, and what kind of requests they accept. These cards help agents find the right collaborators without giving away sensitive implementation details.
Here’s how a typical flow goes:
A user asks the client agent to complete a complex task.
That client agent realizes it needs help and breaks the job into smaller parts.
It reviews other remote agents’ cards to see who’s best for which task.
It sends requests to those remote agents, who get to work in parallel.
They share progress, respond with outputs, or even ask follow-ups.
The original agent pulls all the results together and delivers a final response.
This setup supports more flexible workflows where agents can specialize and dynamically coordinate with one another, especially useful for large, multi-step tasks that benefit from multiple perspectives.
Learn more about how Auth0 is collaborating with Google Cloud to help define the A2A spec

Production-ready AI agents need to be secure, and auth is a big part of security. Auth0 is partnering with Google Cloud to help deliver secure authentication for the Agent2Agent (A2A) protocol.
MCP and A2A: Complementary, Not Competitive
Sometimes, these systems are blended:
- Each agent in an A2A system might use MCP to call their own tools
- Or, a single MCP-powered agent might spin up temporary agents to handle subtasks (LangGraph, AutoGen)
But they solve different problems:
- MCP extends what a single agent can do
- A2A expands how agents can collaborate
Why This Matters for Identity and Security
As AI agents evolve, the need for secure, observable, and identity-aware access grows. Whether an agent is calling a tool via MCP or delegating to another agent via A2A, we need ways to:
- Authenticate agent identities
- Control what they can access
- Trace their behavior
At Auth0, we think a lot about these layers of trust and access. If your agents can make API calls or act on behalf of users, identity becomes just as important as it is for human users.
Conclusion
MCP and A2A are not competing standards, they’re complementary building blocks for how AI agents operate. Knowing when to use one (or both) is critical for developers building the next generation of AI-native apps. Auth0 has a MCP Server you can use today and learn more about our collaboration with Google Cloud on the A2A protocol.
About the author

Will Johnson
Developer Advocate
Will Johnson is a Developer Advocate at Auth0. He loves teaching topics in a digestible way to empower more developers. He writes blog posts, records screencasts, and writes eBooks to help developers. He's also an instructor on egghead.io.
View profile