In the last few years, the FIDO Alliance has been working relentlessly towards the vision of helping users authenticate with maximum security and minimum friction. The resulting WebAuthn standard provides the foundation for that to happen. Now it is up to the industry to make that technology available to end users.
WebAuthn is the only standard-based authentication method that makes phishing impossible, as it binds the public/private key to a specific web domain. You cannot mistakenly authenticate into a phishing website.
A few weeks ago, we announced the support for FIDO Security Keys for MFA using WebAuthn. Security Keys are a great way to secure access to your account, but their adoption is mostly limited to tech-savvy users or corporate environments with relatively high-security requirements.
We are now announcing support for FIDO Device Biometrics for MFA using WebAuthn. This makes the security and convenience of WebAuthn-powered flows available to anybody who has a device and browser who can support the biometric challenge, not just those who have security keys. Now all users can reap the benefits of this technology, regardless of how tech-savvy they are.
Want to learn more about WebAuthn?
Visit → webauthn.me
Enabling users to authenticate using their device biometrics has two benefits: it greatly reduces friction during the authentication challenge, which impacts user retention and revenue, and it increases security since the flow is not phishable by bad actors.
The data we collected during Beta testing shows biometrics performing much better than other MFA options:
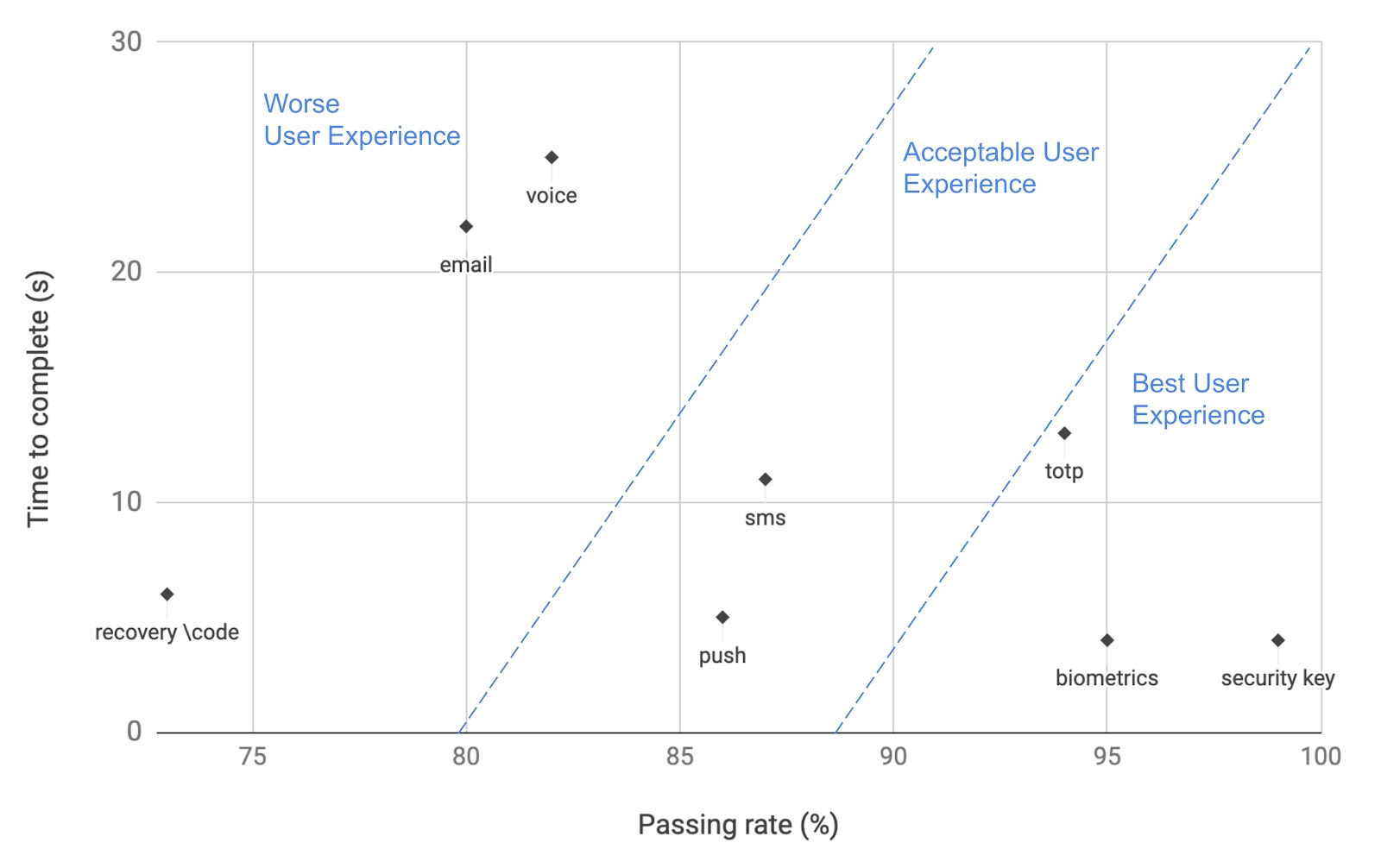
Internal Auth0 study, March 2021
The Y axis shows time to complete, and the X axis represents the % of users that can complete the MFA challenge. WebAuthn platform authenticators have the highest passing rate (94%) and the shortest time to complete (5 seconds).
WebAuthn With Device Biometrics Availability
For users to take advantage of biometric authentication on the web, they need to have devices that support WebAuthn. It’s hard to know precisely how many devices are capable of WebAuthn Device Biometrics, as there is no specific information. We can only approximate with operating system and browser usage statistics, as in Android and Windows, it depends on the device in addition to the OS/Browsers.
| Operating System & Browsers with WebAuthn Device Biometrics Support | OS Adoption March 2021 Source: StatCounter |
| Mac OS Catalina (Chrome, Edge, Brave) | 67% |
| Mac OS Big Sur (Chrome, Edge, Safari, Brave) | Unknown |
iOS 14+ (Safari) | 76.24% |
Windows 10 + (All modern browsers) | 78.28% |
Android 7+ (Chrome) | 82.08% |
You can get additional information about browser support on our webauth.me site.
Enrolling With Device Biometrics
Authenticating using WebAuthn with Device Biometrics presents two unique challenges:
- Given the authentication method is bound to a specific device, it cannot be the only authentication method the user has, or they will be unable to log in from a different device.
- Users would want to use biometrics to login from all of their devices, and applications should make it possible to enroll all of them.
Auth0’s solution addresses both problems. It will always ensure that users’ have another way to authenticate. When MFA is enabled, users can only enable biometric authentication if they also enable another option.
The enrollment flow would be as follows:
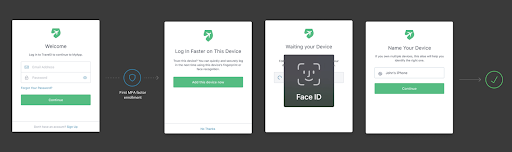
- The user authenticates with a username and password.
- Enrolls in any other MFA Factor (e.g., a security key, a TOTP application like Google Authenticator, Push, SMS)
- If the device is capable of using Webauthn Device Biometrics, users will get the option of enrolling with it.
- If they do, the next time they login from that device, they can use Device Biometrics as the second factor.
Progressive Enrollment
Auth0 employs progressive enrollment to aid users in authenticating from different, WebAuthn-capable devices. Whenever a user presents this type of device for authentication, they will first be prompted to enroll it. This is a progressive process that is only activated once new, WebAuthn-capable devices are used so that they will be able to authenticate with biometrics in all of their devices capable of this functionality.
For example, when a user initially authenticates from a MacBook with a Touchbar, they authenticate with their username and password and enroll in another MFA factor. However, since the MacBook has biometric capabilities, they will be prompted to enroll if they like. Later, if they wish to use their iPhone with FaceID capabilities, they will be automatically asked to use Face ID before proceeding. This process guides users through a progressive enrollment flow that is easy, seamless, and friction-free.
Here’s a quick demo of WebAuthn with Auth0:
Enabling WebAuthn With Device Biometrics
If you are currently using MFA with Auth0, biometrics can be enabled from the Auth0 dashboard.
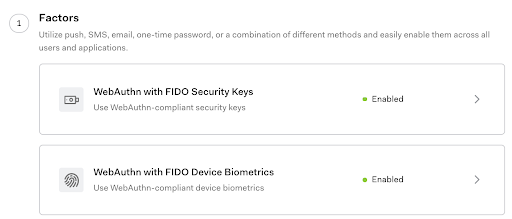
After you enable it, users will receive prompts from enrolling their devices when authenticating; no code change is necessary.
Please refer to our documentation to learn more about Auth0’s WebAuthn implementation in general and WebAuthn for Device Biometrics specifically.
What’s Next
WebAuthn with Device Biometrics combines two authentication factors in one: something you have (the device) and something you are (the biometrics). In case you can’t use biometrics in the device, e.g., if you are wearing a mask, you’ll use something you have plus something you know (the passcode). As it’s stronger than a password and simpler to use, the next step is bringing it to passwordless authentication. Auth0 will support this in the same way we are doing it for MFA by letting users progressively enroll all of their devices. Stay tuned!
About the author

Andrés Aguiar
Product Manager
I’ve been at Auth0 since 2017. I’m currently working as a Product Manager for the Auth0 FGA and OpenFGA products. Previously, I worked in the teams that owned the Login and MFA flows.
I spent my entire 20+ year career building tools for developers, wearing different hats. When I'm not doing that, I enjoy spending time with my family, singing in a choir, cooking, or trying new kinds of local cheese.
