In the context of modern application security, access tokens play a prominent role in authorization. They are the digital keys that grant applications access to protected resources on behalf of a user. However, with great power comes great responsibility. A compromised access token can be a significant security liability. This is where the principle of least privilege (PoLP) becomes not just a best practice, but a critical defense mechanism.
This article takes a deep dive into the intersection of access tokens and the principle of least privilege, with a focus on leveraging the capabilities of OAuth 2.0 to build more secure and resilient systems. We'll explore the foundational concepts, advanced techniques, and provide a practical checklist for your security reviews.
What Is the Principle of Least Privilege?
The principle of least privilege is a core concept in computer security. It states that users, programs, or processes should only be granted the minimum permissions necessary to perform their function. In other words, every component within a system should operate with the lowest possible level of access, or "privilege," required for its tasks.
Think of it like giving keys to a building. Instead of giving every employee a master key that opens every door (high privilege), you give each person only the keys to the specific rooms they actually need to access (least privilege). For example, a receptionist gets a key to the front desk area, a developer gets a key to their office, but neither has access to the executive offices unless explicitly required.
This approach enhances security by limiting the potential damage from an accident, error, or security breach. If an account with limited privileges is compromised, the attacker's access is confined to a small controlled area, preventing them from gaining control over the entire system. Therefore, applying this principle means ensuring that applications and users can only access the specific data and perform the exact actions they are explicitly authorized to do, and nothing more.
OAuth 2.0 and Its Role in Access Control
At its core, OAuth 2.0 is an authorization framework, not an authentication protocol. This distinction is crucial. While authentication is about verifying identity, authorization is about granting permission to access specific resources. OAuth 2.0 provides a standardized way for a client application to obtain an access token from an authorization server, with the user's consent, to access resources hosted by a resource server.
A solid grasp of the OAuth 2.0 components is essential for implementing the principle of least privilege. Let’s quickly recap them:
- Roles:
- Resource Owner: The user who owns the data and grants permission to the application.
- Client: The application requesting access to the user's data.
- Authorization Server: The server that authenticates the resource owner and issues access tokens after obtaining their consent, e.g., Auth0.
- Resource Server: The server that hosts the protected resources and accepts access tokens for authorization, typically implemented as an API.
- Tokens:
- Access Token: A credential used by the client to access protected resources. It represents the authorization of a specific client to access specific resources.
- Refresh Token: A long-lived credential used to obtain a new access token when the current one expires.
- Scopes: The mechanism within OAuth 2.0 that allows us to define the granular permissions a client can request.
With this basic knowledge, let's delve deeper into how to implement the LP principle in a system protected by access tokens.
For a deeper understanding of OAuth 2.0, consider reading OAuth 2.0 and OpenID Connect: The Professional Guide.
Scopes: The Heart of Least Privilege in OAuth 2.0
The true power of OAuth 2.0 in enforcing the principle of least privilege lies in the effective use of scopes. Scopes are strings that define the specific permissions a client application is requesting. Unlike OpenID Connect, OAuth 2.0 does not define standard scopes. The scopes used in an application scenario depend on the specific business case. Specifically, they are defined by the resource server (API) implementer and must be known to the client application. When designing the scopes for your API, follow a few best practices.
No scopes, No party!
While the OAuth 2.0 specification does not explicitly forbid a client from requesting an access token without a scope parameter, doing so represents a significant security anti-pattern and a direct violation of the principle of least privilege.
When a client initiates an authorization request without specifying any scopes, the authorization server's behavior can be ambiguous. Since the OAuth 2.0 specifications do not define a standard behavior to handle this case, your application can receive an error message or a subset of predefined scopes, possibly empty.
Moreover, if API implementations do not accurately check scopes, you may find yourself in a scenario where the issued access token essentially grants the full permissions of the user.
This practice carries substantial risk. If a scopeless access token is compromised—leaked from a client-side application, intercepted in transit, or exfiltrated from a backend system—the attacker gains broad, unrestricted access to the user's resources. They could potentially read sensitive data, modify information, and perform actions on behalf of the user, all because the token's power was not constrained.
As a result, avoid scopeless access tokens. Always include the scope parameter in your application's authorization requests, and make your APIs always check for the expected scopes.
Designing granular scopes
Vague or overly broad scopes defeat the purpose of least privilege. Consider an e-commerce API. You may think of scopes like orders or profile to allow access to the user’s orders and profile. However, these scopes are not explicit on the type of access they grant. Probably the orders scope says that your application can manage orders, i.e., it can read, create, update, print, for example. A more granular approach would be:
orders:read: Allows the client to read a user's order.orders:write: Allows the client to create new orders.profile:read: Allows the client to read the user's profile information.profile:write: Allows the client to update the user's profile.
This granularity ensures that a third-party analytics dashboard, for example, would only ever request and be granted the orders:read scope, mitigating the potential damage if its access token were to be compromised.
The following picture visually summarizes the application of the principle of least privilege using granular scopes:
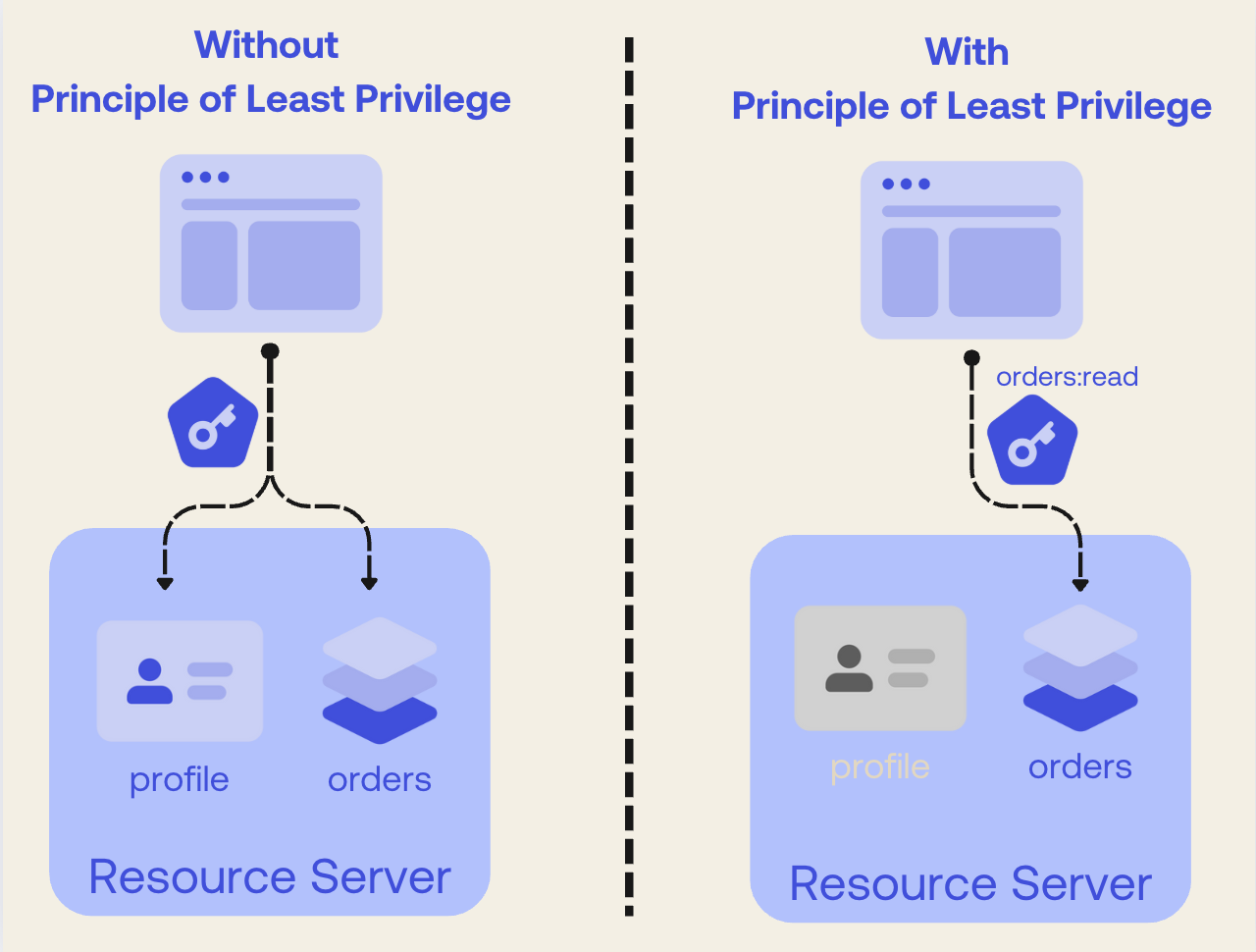
Leveraging hierarchical scopes
OAuth 2.0 does not strictly specify the format of scopes. They are generic strings whose meaning depends on the API context. As illustrated in the examples above, a common approach is to use the format resource:action. Some use the dot (.) as a separator instead of the colon (:). It really does not matter.
While you are free to use the format you prefer, consider taking advantage of the hierarchical structure of the format suggested above. For example, if you want to grant access only to the status of an order for informational purposes, but not at the details of the order, you can define a scope like orders:status:read. This allows you to have more granular control over a protected resource.
For more advanced scenarios, you may consider using OAuth 2.0 Rich Authorization Requests, which allows you to specify detailed authorization requests.
Using dynamic scopes
Modern applications often require different levels of access at different times. Instead of requesting all possible permissions upfront, a better user experience and security practice is to request scopes dynamically as needed. For instance, an application could initially request profile:read on user sign-up. Later, when the user wants to perform an action that requires more permissions, such as updating their profile, the application can initiate a new OAuth 2.0 flow to request the profile:write scope. This adheres to the principle of just-in-time access.
Ensuring user consent
User consent is a critical component in OAuth 2.0 authorization requests, directly supporting the principle of least privilege.
The authorization server must obtain explicit approval from the user, ensuring they understand and consent to the specific access an application client is requesting on their behalf. This consent should be freely given, with adequate information provided to the user.
In this context, a user-friendly description of the scopes a client application is requesting is key. The user should be aware of the permissions they are delegating to the application.
A key aspect is that scopes do not create new permissions; they merely represent a subset of the permissions the user already possesses and delegated to the client application.
Beyond Scopes: Advanced Token Security and Validation
While scopes are the primary tool for defining what an application can do on behalf of the user, a comprehensive strategy for least privilege involves more than just well-designed scopes. You must also consider the entire lifecycle of an access token.
Token validation best practices
At the resource server, every incoming access token must be rigorously validated before granting access. This validation should go beyond simply checking the token's signature and expiration. Here are the fundamental steps to validate an access token before granting the application access to the resource:
- Signature Verification: Always verify the token's signature against the authorization server's public key. This ensures the token was issued by a trusted source and has not been tampered with.
- Expiration Check: Check the
expclaim to ensure the token has not expired. - Issuer and Audience Validation: Verify the
iss(issuer) andaud(audience) claims. Theissshould match the expected authorization server, and theaudshould match your resource server. This prevents tokens issued for one application from being used to access another. - Scope Enforcement: This is the critical step for least privilege. The resource server must check the
scopeclaim in the access token and ensure that the requested action is permitted by the granted scopes. - User Permissions Check: Last but not least, make sure that the resource your application is requesting to access is actually accessible by the user with the permissions matching the scopes. Read this article to learn more about this.
Short-lived access tokens and refresh tokens
In addition to a correct design and use of scopes, the management of access tokens is a critical security component adhering to the principle of least privilege. A key strategy to bolster security is the implementation of short-lived access tokens. The rationale behind this approach is to drastically reduce the "window of opportunity" for a potential attacker. If an access token, which grants an application permission to access specific resources, were to be compromised, its utility would be severely limited by its short lifespan.
Typically, these short-lived access tokens are issued with a validity period ranging from a few minutes to a few hours, depending on the business case and the security level required.This brevity is a deliberate security measure connected to the principle of least privilege: not only your application must have the minimum permissions it needs, but it must have them for the minimum amount of time necessary. However, to ensure a seamless user experience without requiring re-authentication every few minutes, a complementary mechanism is employed: refresh tokens.
When an access token expires, the client application can use the refresh token to request a new, valid access token from the authorization server. This process is transparent to the user, maintaining a continuous session.
Given their power to grant new access tokens, refresh tokens themselves must be securely managed to prevent security issues. Learn more about refresh tokens by reading this article.
Want to get up to speed with OAuth2 and OpenID Connect?
Download the free ebook
Security Review Checklist for Access Token-Based Systems
To assist in your development and review process, here is a checklist to help ensure you are adhering to the principle of least privilege and other access token security best practices.
Scope and Permissions
- Are scopes granular and well-defined, following the principle of least privilege?
- Does the application request only the necessary scopes at any given time?
- Is there a process for users to review and consent to the requested scopes?
- Are there different levels of scopes for read vs. write vs. administrative actions?
Token Issuance and Lifecycle
- Are access tokens short-lived?
- Are refresh tokens used to obtain new access tokens?
- Are refresh tokens stored securely on the client?
- Is there a mechanism to revoke refresh tokens and access tokens?
Token Validation at the Resource Server
- Is the token's signature verified on every request?
- Is the token's expiration (
expclaim) checked? - Is the issuer (
issclaim) validated against a trusted value? - Is the audience (
audclaim) validated to ensure the token is intended for this API? - Is the
scopeclaim inspected, and are the permissions enforced for the requested operation?
Conclusion
Building secure applications is not an afterthought but a core responsibility. The principle of least privilege is a powerful paradigm for mitigating the risks associated with access tokens. By meticulously designing granular scopes, implementing robust token validation, and managing the token lifecycle effectively, you can significantly enhance the security posture of your applications.
The OAuth 2.0 framework provides the tools necessary to implement a least privilege model, but it is your responsibility as developers to use them correctly and diligently. By following the best practices and using the checklist provided, you can be more confident in the security and resilience of your access token-based systems.
About the author

Andrea Chiarelli
Principal Developer Advocate
I have over 20 years of experience as a software engineer and technical author. Throughout my career, I've used several programming languages and technologies for the projects I was involved in, ranging from C# to JavaScript, ASP.NET to Node.js, Angular to React, SOAP to REST APIs, etc.
In the last few years, I've been focusing on simplifying the developer experience with Identity and related topics, especially in the .NET ecosystem.
