Credential stuffing is a type of cyberattack in which a cybercriminal uses stolen usernames and passwords from one organization (obtained in a breach or purchased off of the dark web) to access user accounts at another organization.
Credential stuffing attacks are one of the most common causes of data breaches because 64% of all people reuse the same password on multiple (and sometimes all) accounts. In fact, on Auth0's platform alone, nearly half of all login requests we receive each day are attempts at credential stuffing.
The opportunity for cybercriminals to use credential stuffing is only growing as more credentials are exposed through breaches; at present, literally billions of compromised credentials are circulating on the dark web.
However, credential stuffing attacks are preventable if you implement the right cybersecurity measures. Below is what executives need to know about credential stuffing attacks and what can be done to reduce or prevent the likelihood that their organizations will be a victim of one.
More in the following:
How Credential Stuffing Works
To execute a credential stuffing attack, cybercriminals add a list of stolen username and password pairs to a botnet that automates the process of trying those credentials on multiple sites at once. Large-scale botnet attacks can overwhelm a business' IT infrastructure, with websites experiencing as much as 180 times their typical traffic during an attack.
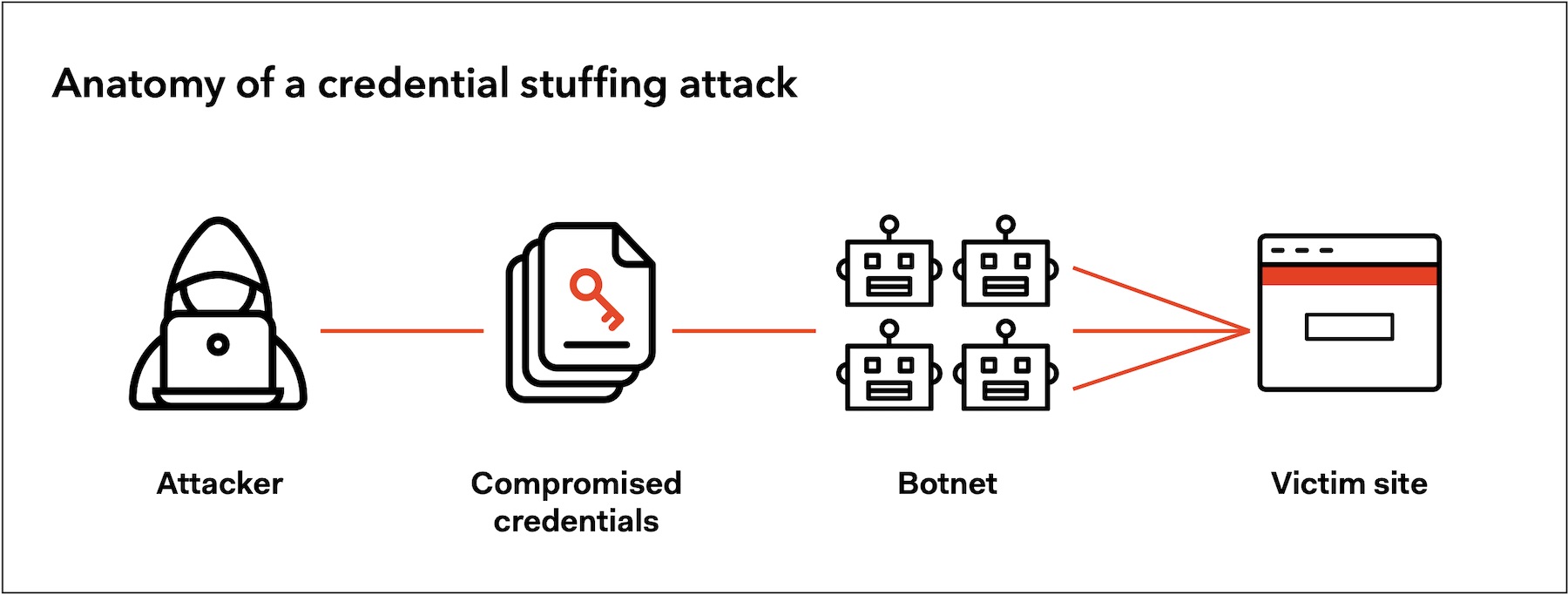
Once cybercriminals find a site where a set of credentials works, they’ll have access to a user's account and personal data to do with as they please, which most commonly includes:
- Selling access to compromised accounts: This is particularly common for media streaming services. Disney+, Netflix, and Spotify have all been victims of attacks in which hackers sold access to user accounts for less than the cost of a subscription.
- E-commerce fraud: Hackers can impersonate legitimate users at retailers' websites and order a high-value product, either for their own use or for reselling. This is a common (and for criminals, potentially lucrative) form of identity theft, which makes retail the most vulnerable vertical for credential stuffing, according to research from Akamai.
- Corporate/institutional espionage and theft: While the above crimes have serious consequences for companies and their customers, this third form of attack has the potential to be most devastating for businesses. If an attacker successfully hijacks the account of an employee or admin, they could gain access to all sorts of sensitive personal information, like credit card numbers, social security numbers, addresses, and login credentials as well, all of which they can sell to the highest bidder.
The Costs of Credential Stuffing Attacks
Although credential stuffing attacks often have a low success rate (usually one to three percent), their impact on organizations is often anything but small.
For example, the Ponemon Institute's "Cost of Credential Stuffing" report found that businesses lose an average of $6 million per year to credential stuffing in the form of application downtime, lost customers, and increased IT costs.
Increasingly, regulators, as well as the public, are also holding companies accountable for credential stuffing attacks with stiff fines. Companies may be subject to legal action under data privacy laws such as GDPR if they fail to implement adequate security measures to prevent such attacks, fail to inform the public of a breach, or don't do enough to protect passwords.
For example, in 2018, the UK's Information Commissioner's Office (ICO) fined Uber £385,000 for "a series of avoidable data security flaws" that exposed the data of approximately 2.7 million UK customers. And in 2021, the French Data Protection Authority (CNIL) fined a data controller and its data processor €225,000 “for failure to implement adequate security measures to protect customers’ personal data against credential stuffing attacks on the website of the data controller.”
Credential Stuffing Attacks vs. Brute Force Attacks
Credential stuffing is considered a type of brute force cyberattack. But in practice, the two are very different, as are the best ways to secure your systems against them.
Brute force attacks attempt to guess passwords by changing the characters and numbers (often in prescribed patterns or with commonly used base password phrases). To protect against them, you can limit the number of failed login attempts with brute force protection, use a CAPTCHA, or require your users to use a stronger password.
However, a strong password won’t stop a cybercriminal from gaining access to an account via credential stuffing because the password is already known. Even CAPTCHA's or brute force protection’s ability to protect users is limited since users often change their passwords in predictable patterns and cybercriminals have a breached password to iterate from.
How to Prevent Credential Stuffing Attacks
Most people know password reuse is unsafe but choose to use the same password on multiple sites anyway because they have roughly 100 passwords to remember. Password managers are an option, but adoption rates are low. So to prevent credential stuffing attacks, it’s up to organizations to take measures — such as removing passwords altogether — to ensure cybercriminals can’t use stolen credentials to access their users’ accounts. Based on OWASP's Credential Stuffing Prevention Cheat Sheet, below are several methods for doing so.
Credential hashing
Credential hashing is the first step to protecting your user's credentials from theft. Hashing scrambles a user's password before you store it in your database so that in the event that it is stolen, a hacker won’t be able to use them (in theory, at least).
In practice, not all password hashing is uncrackable. As Rick Redman, a penetration tester at KoreLogic, explains, “The strength of the hash is the insurance policy. It tells you how much time users have to change their passwords after a data breach before they come to harm... If it’s just SHA1, there is no window... If it’s bcrypt, you have time to run away and change all your passwords.”
So although hashing user passwords won’t prevent a credential stuffing attack, it will limit what a cybercriminal can do with those passwords once they’ve stolen them.
Breached password protection
Breached password protection compares the password a person uses to log in against databases of compromised credentials (like haveibeenpwned) to prevent credential stuffing in real-time.
For example, Auth0's breached password detection can be configured to notify a user, block them from logging in, or request an additional authentication factor (MFA) if it suspects their credentials were part of a published security breach or if a login attempt came from a suspicious IP address.
Bot detection
As mentioned earlier, attackers use bots to execute a credential stuffing attack. Auth0's bot detection feature is able to identify a bot attempting to authenticate with a high percentage of success. It provides protection against credential stuffing attacks with very little friction to legitimate users. When a bot attack is detected, it displays a CAPTCHA step in the login experience to eliminate bot and scripted traffic.
Anomaly detection
Monitoring what is happening is always a good approach to intervene earliest and stop an attack. If you have visibility of your traffic, you can understand when you are under attack, and you can take action to mitigate attacks. In Auth0, you can use Log Streams to monitor your traffic in near real-time. After creating and configuring a Log Stream, you will start seeing Auth0 events being ingested into your chosen monitoring service. Based on your monitoring service, you can build your anomaly detection dashboard by anayzing the Attack Protection Log Events.
Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) is a highly effective way to prevent credential stuffing because it requires users to log in with another form of authentication in addition to a username-password combination. For example, this could mean biometric authentication such as a fingerprint, a one-time code sent to a device associated with the user, or an email sent to a secured account — none of which a cybercriminal will have access to.
Although the adoption of MFA has been slow due to concerns about its impact on customer experience, the increase in sophistication and customizability of MFA are helping it catch on. For instance, in February 2020, Google announced it would require Nest smart home users to use two-factor authentication.
Continuous authentication
Continuous authentication systems use factors like biometrics or behavioral patterns to verify a user’s identity in real-time (while they use an application) instead of a password. As a result, credential stuffing attacks (as well as a number of other cyberattacks) are no longer a viable method for cybercriminals to gain unauthorized access to a user’s account.
Passwordless authentication
Passwordless authentication can prevent credential stuffing altogether because it verifies a user with something they have (a device or another account) or something they are (biometrics) instead of a password (something they know). Passwordless also creates a better login experience for users and saves organizations time and money from dealing with password resets.
Passwordless Authentication Is Better for Businesses and Users
Not only does passwordless authentication eliminate credential stuffing attacks, but numerous studies and reports show that it is a more secure, more user-friendly, and more cost-effective solution overall than traditional username-password authentication for both businesses and their users.
“Relying on passwords as the primary means for authentication no longer provides the security or user experience that consumers demand,” Andrew Shikiar, Executive Director of the FIDO Alliance, explains in a joint report with the World Economic Forum. Adrien Ogee, Project Lead from the World Economic Forum, adds, “Better authentication practices are not just possible; they are a necessity.”
Auth0’s platform makes it easy to implement secure, user-friendly passwordless authentication using biometrics, social logins, and more. Learn how to eliminate the risks associated with traditional username and password authentication with Auth0’s Passwordless authentication platform here.
About the author

Diego Poza
Sr Manager, Developer Advocacy (Auth0 Alumni)
